Introduction to Signals and Analysis
G’day, Folks! Thanks for coming to my presentation Introducing Signals Intelligence. Called SIGINT for short. My name is Tristan de Alwis.

Let me get a bit of self-promotion out the way. I studied at the University of Rochester for Biomedical Engineering and Data Science. After graduating, I quickly found myself in the Defense Sector starting with L3Harris working in the ISR segment (That’s Intelligence, Surveillance, and Reconnaissance) and then later on in Space Systems developing advanced Computer Vision solutions to satellite imagery and Geospatial Intelligence for an Intelligence Agency. And then most recently, I was a Sr. Data Scientist at Booz Allen Hamilton using my skills in Natural Language Processing and Large Language Models for the Intelligence Community as well as helping educate Department of Defence personnel on AI and how they can use it in their programs and recruit the right talent for those use cases.
Now I’m an independent contractor running Otter Solutions, LLC which is a minority owned small business, so if you are a federal agency or defense contractor looking for my set of skills
I encourage you to reach out to me either on my website, e-mail, commenting on this video, or LinkedIn.
https://www.otter-solutions.com/ https://www.linkedin.com/in/tristan-de-alwis/

Okay, sorry to murder your ears with my gloating, let’s move on to today’s topic of SIGINT. The Agenda I have is to explain and help you understand what SIGINT is. What are its possibilities and potential future work with examples! Because who likes a powerpoint without images?

Great! Let’s start with defining SIGINT.

Signals Intelligence as defined by the National Security Agency, or NSA, is
the type of intelligence derived from electronic signals and systems used by foreign targets, such as communications systems, radars, and weapon systems.
Now why do I specifically look to the NSA?

Because they are the leader of Signals intelligence at the federal level. We have agencies that specialize in different intelligence types such as human intelligence, HUMINT, handled by CIA, measurements and signatures int, MASINT, by DIA, imagery int, IMIINT, by NGA, and so on. All of these may touch other intelligence types, but they specialize because of the created charters at their inception.

This is not to be confused by the Intelligence Community which encompass these agencies as well the Departments of Army, Navy etc, ATF, FBI, Treasury, and so on under the Office of the Director of National Intelligence, or ODNI for short. Okay, Let’s not get carried away by all that now. I plan on making more educational materials on these Intelligence types specifically GEOINT, but comment below what you would like to see.
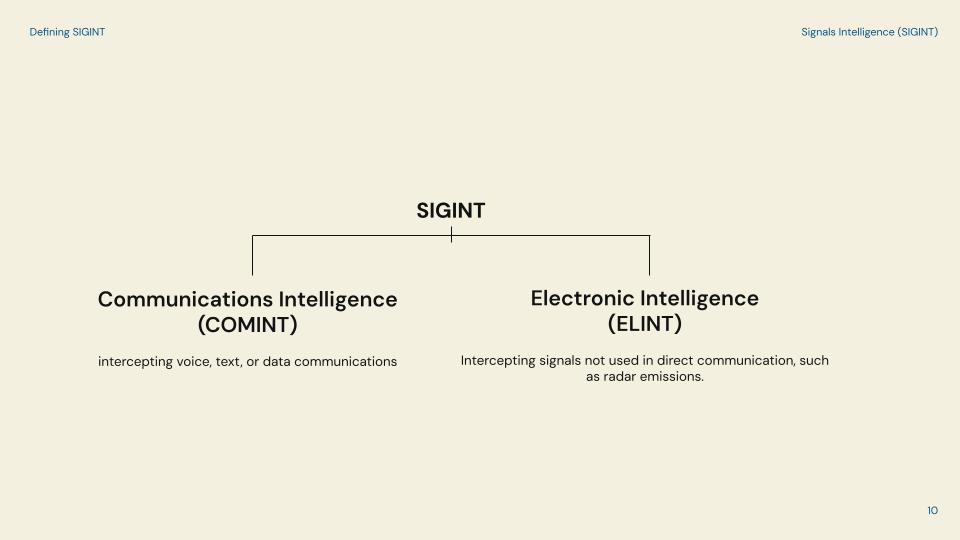
Back to SIGINT. This type of intelligence includes Communications and Electronic Intelligence. COMINT, is about intercepting voice, text, or data communications so think humans trying to communicate with other humans. Versus, ELINT, which is intercepting signals not used in direct communication, such as radar emissions. So think computer systems connecting to other computer systems.

If you’re new to SIGINT, you might ask why this INT type is so important. Great question! Well, there are numerous threats whether nation states, state-funded terrorists, or others that communicate in a variety of ways thanks to the digital age, and I would say it behooves our defense experts, strategists, military planners to know what they are saying, planning, doing or not doing to prevent harm to our national interests. It almost insists upon itself. Furthermore, by also continuing our practice, research, and development in SIGINT, it allows us to be more adept at strengthening and protecting our own communications. Essentially, competition will bring out the best in us. Lastly, we need to be able to assimilate with other INT sources to produce what we call “All-Source Intelligence.” This is the end goal of collection and analysis. Think about what’s being briefed to the President, Congress, Secretary of Defence and other state officials at the end of the day in order for them to make the important decisions of great national importance they need all source intelligence

Now that I’ve beaten a dead horse, let’s get into some more technical aspects. To start, how do we classify what is a signal?

Well to start with base knowledge it’s any form of communication that requires a transceiver, the technical term for a sender, and a receiver, the term for a listener. So examples would be anything using a radio frequency. Wi-Fi, Bluetooth, FM/AM Radio, Satellite Communications, Mobile Communications. Yes, your phone is a radio. It’s a very smart radio. It has an internal antenna, and it emits signals and it just has a whole bunch of other stuff wrapped around it.
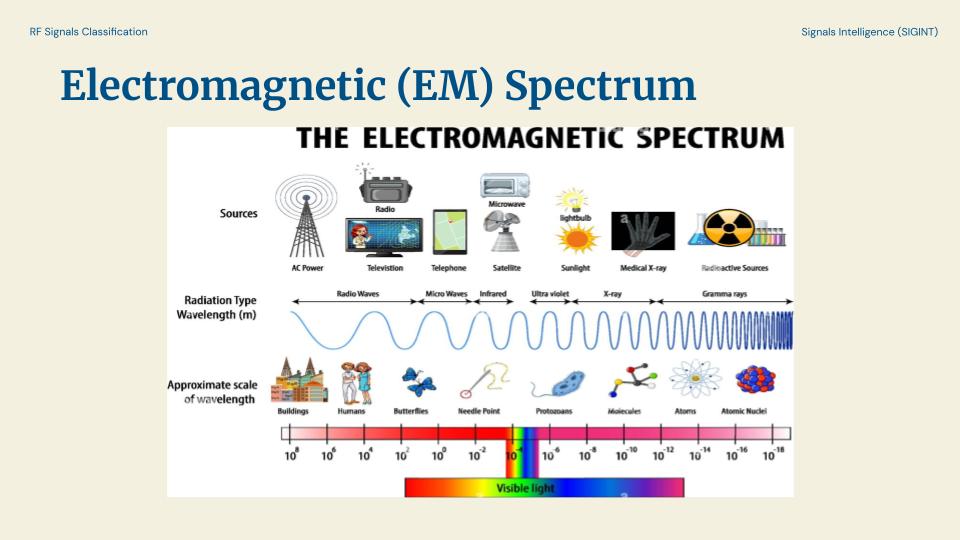
These all operate on the Electromagnetic (EM) Spectrum. Shown here in this figure we can illustrate the wavelengths at which we can see visible light and not see infrared light, and other classifications of wavelengths.
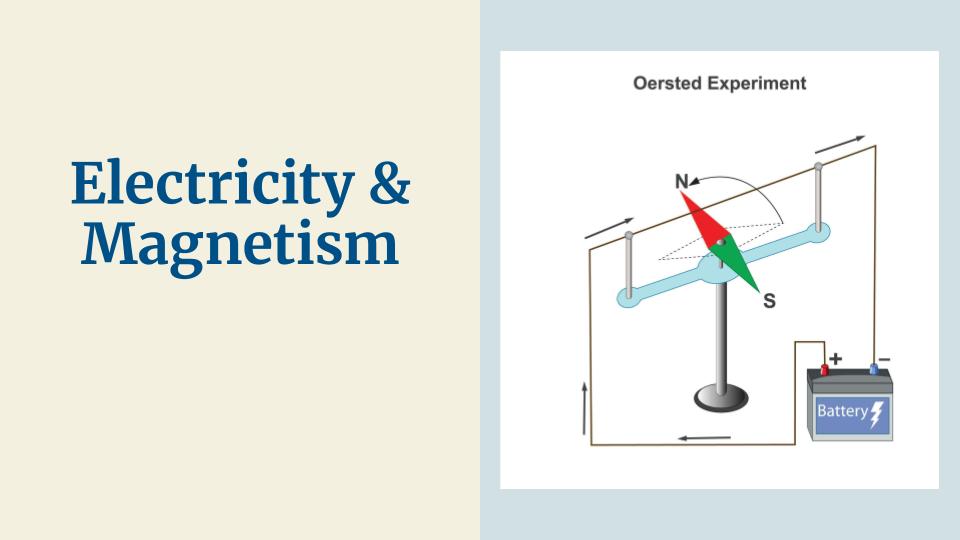
Electromagnetism is the physics of electric and magnetic fields. If you didn’t know, electricity and magnetism are related. Magnets produce a magnetic field which alter electric currents and vice versa. So here in this figure is an electrical current and it produces a magnetic field that is influencing a magnetic dipole in this case a compass. There are 4 equations called Maxwell’s Equations that mathematically explain this phenomena, but that’s for another lecture.

Now that we know what is a signal, how do collect it?

For our purposes of defense and intelligence, we break this into 4 areas. Land, Air and Sea shown here have a variety of platforms. On land, we’re all familiar with cell phone towers, or dishes you might see on homes for TV also now Starlink for satellite internet. But you’ve maybe seen pictures of “spy sites” that have large spheres. Basically, all these are some sort of antenna capturing the energy and waves produced on the spectrum. For Air, we have planes and jets we could be trying to listen to other foreign fighter jets, detect Radar, or there air/surface emissions.

Couple years ago the big thing was the Spy Balloon that traversed over the US. Some people wanted to shoot it down with their granddaddy’s rifle. The PRC was probably using it as some sort of collection platform. And of course by Sea. There is the famous story of Midway back in WWII. The US intercepted Japanese Naval communication and were able to counter-ambush Japanese vessels at the Battle of Midway. This was a significant achievement all thanks to signals intelligence and cryptography

I mentioned there are 4 areas, but I have only listed 3 here. Can you guess the 4th? It’s basically where any Hollywood movie goes if you’re in the 10th sequel… That’s right. Space! Since the Space race in the 60s, several nations are now heavily invested in space exploration and putting a great deal of systems that orbit the earth for commercial reasons but also militarily. Certainly a big one you can imagine is communication. In the 90s, tracking Osama bin Laden’s and Taliban leadership movements and plans was done largely by satellite phone communication.

Alright, moving on. Once we have intercepted some signals, what do we do with it?! Well we analyse it of course! Yes, we!

Because who can do analysis? You can, I can, Army signal analysts, navy cryptographers, Air force electronic warfare technicians, RF engineers, computer engineers, you name it. It’s gotten a lot simpler these days with off the shelf products, and the federal government has put a lot of resources into funding these developments so there is a large industry afloat because of this need.

What can we do with analysis? Well, depending on your use case, we can locate the transmitter, or at least a general direction and distance, determine who is transmitting, who is the intended receiver in some cases, or even track what is transmitting because most things have a unique signature due to manufacturing inconsistencies in the hardware. We may even want to conduct a man in the middle attack which is where we intercept a message and transmit a false message to the intended receiver instead. That can have a lot of consequences to an adversary. Or simply to overload and block that channel making it impossible for our adversary to use that communication method.

When and where can we do Analysis? Anytime! Anywhere! The Electromagnetic spectrum is omnipresent. These waves that are carrying data radiate everywhere. It is entirely difficult to transmit in secret. There are tools designed to continually listen to bandwidths of frequencies and detect changes. Now of course, you can encrypt this data but nonetheless, when you send a signal anyone can still detect the signal that you are radiating that you are propagating.
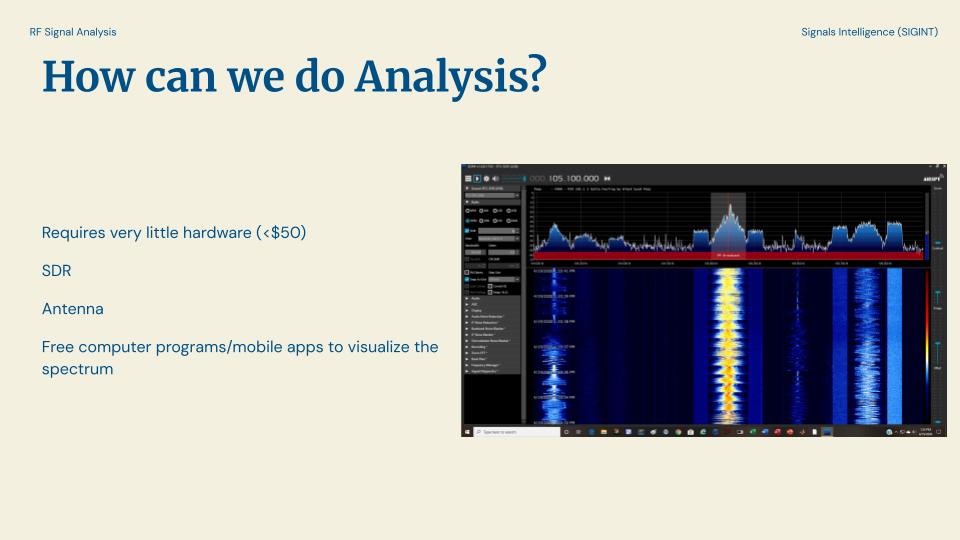
How can we do analysis? It’s very inexpensive now. For less than $50 you can pick up Software Defined Radio, antenna, and free computer software tools. SDRs are cheap devices that let you visualize the spectrum around you and see the energy and wave forms around you. If you don’t want to spend any money, people post live feeds of the spectrum around them online or specific radio frequencies online so you can use their collection data. And then you can use those computer programs to analyse what your listening, speech detection etc.

In conclusion

The EM Spectrum has endless possibilities and being able to understand what is operating on the spectrum is the driving force of Signals Intelligence. It’s pretty much here to stay until some physicist/researcher invents a new form of communication that does not produce a signal of any sort maybe telepathy but even then the science fiction isn’t all worked out. So I do not see that in the near future.

I appreciate you listening. Let me know if you have questions. If you have a need for a computer scientist, software engineer, data scientist, let’s discuss. I am available.
Cheers!


Leave a Reply to A WordPress Commenter Cancel reply